What is the Crypto Bone?
In short, the Crypto Bone is a novel approach to making confidential communication both secure and usable.
While you are writing or reading messages on your Linux computer, the security of your communication is always at risk, because malware can affect your computer in many ways. The computer we use day-by-day essentially is too complex and too vulnerable to be completely secure.
It is quite obvious that in using a second external device to encrypt your messages, security can be improved considerably. The original idea was to use an autonomous micro computer like the Beagle Bone or the Raspberry Pi to delegate all encryption and key management to a device that can be much more secure than the computer you usually use.
Such a secure, external device can help ordinary users to establish secure communication with other people that is always encrypted. And the AES encryption keys reside only in the two endpoints providing reliable end-to-end message encryption.
And at the same time it will make life easier for people, because all message keys are stored in a safe place. Apart from providing a single secret when a conversation with somebody starts, there is no need to keep track of the message keys used to encrypt the messages that are sent out. These keys are updated and managed automatically in a safe manner, so that the user is not required to remember keys or complex passwords to continue the secure communication.
It is your login password that you'll need to run the graphical user interface, because the keys are stored in the memory of a daemon that can only be used with root permissions.
Users don't need any knowledge of cryptography or special skills to operate the Crypto Bone. And they still maintain the sole control over the message keys themselves, as it possible to interrupt or reset the initial secret for any communication using the graphical user interface.
Although such a separate, external device is quite useful to secure the database in which message keys are stored, it is also possible to use a carfully designed daemon on the main machine to be used as a local, software-based Crypto Bone. Obviously the local Crypto Bone is less secure than an external device, but with a carefully designed daemon process it can protect all message keys against malware threats that don't gain full root privilege on the main machine.
The Crypto Bone makes sure that all messages are encrypted with keys stored locally in a safe place, either inside the local cryptobone daemon on your main computer or in a separate external device, if additional protection of the message key data base is required. No third party needs to be trusted to make secure confidential communication happens. It's all under the user's control.
The system updates the message encryption keys with every message exchange, so that only currently used message keys are in the computer's main memory. Past messages have been read already and their decryption keys are reliably deleted and forgotten. This mechanism ensures that messages exchanged in the past cannot be read, even if the encrypted messages are leaked, because the encryption keys, previously stored in main memory, are long gone and cannot be re-constructed.
Benefits
The Crypto Bone:
- makes sure, that all messages are sent encrypted with a strong random message key, so you don't need to bother about using encryption software on your main computer,
- keeps track of your correspondent's message keys and stores them safely in its own isolated data base, so you can forget about encryption keys in every-day use of your Crypto Bone,
- is build on basic principles, like minimal complexity and audited crypto code, so you benefit from the reliability of a well-designed isolated system. In principle, the Crypto Bone can be checked whether it does what it should do and nothing else,
- produces encrypted messages in OpenPGP format, that other people can read, so you are not tied to a propretary system that can only talk to itself. Other people can respond to your secure messages in the same way, even if they don't have a Crypto Bone installed that does all the hard work for them,
- enables you (and only you) to block a correspondent or reset this person's key, so you will always be able to determine how your Crypto Bone works.
You'll only find message in your inbox that you authorized to be accepted by your Crypto Bone.
How does it work in practice?
Using the Crypto Bone for confidential communication starts with downloading and installing one of the main packages If you don't want to store your message keys on a separate device, that's all you need to do. You can use the local, software-based Crypto Bone (ALLINONE) that is included in the main "cryptobone" package.
Just type "cryptobone2" in a shell (or click the icon) to start your Crypto Bone control program.
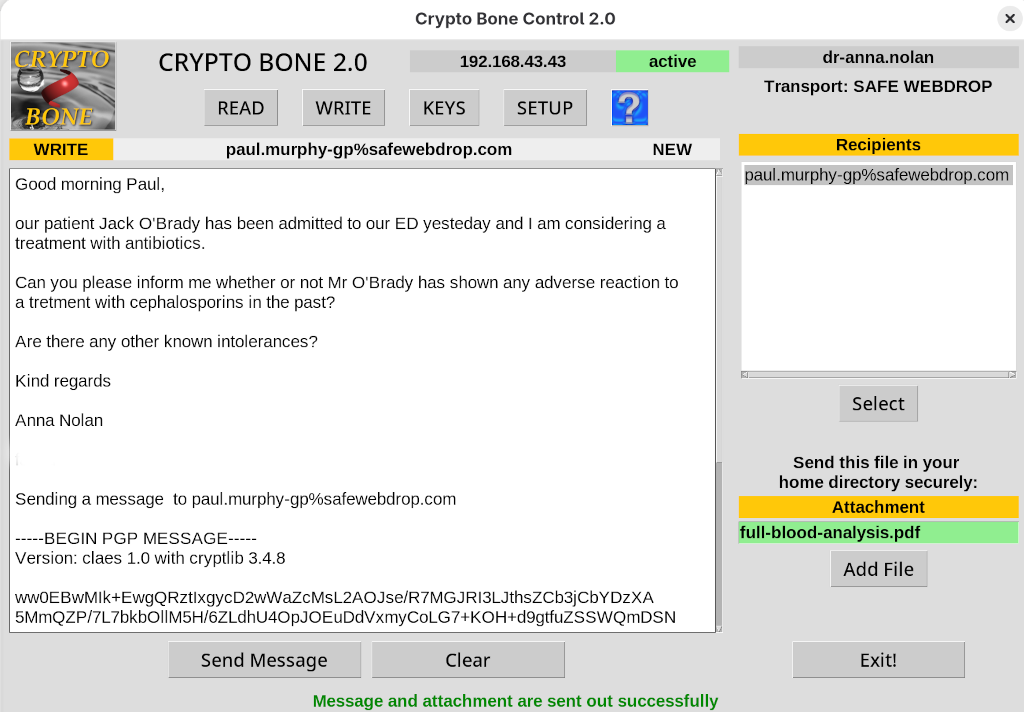
You can control every aspect of your secure communication needs from this GUI program on your main Linux machine.
Using an External Device
If you have decided to use an external device to store the message keys in an isolated environment, you have a number of options. Almost anything with a 64 bit CPU can be used as an external device, not just a microcomputer.In this case, the graphical application on your main computer sends all commands directly to your external device instead of processing the message encryption inside the local daemon on your main machine.
With the second Linux computer you need to activate the external Crypto Bone software that is already installed with the main package. A separate GUI "external-cryptobone-admin" will lead you through the process of activation. If you wish to use such an external device you'll find essential information in the Installation Tutorial.
What you need to do yourself
There are some important tasks the Crypto Bone cannot do for you, because you want to be in control of the whole process. In particular, you need to provide an initial secret that you have agreed upon with your correspondent to start exchanging messages securely.
This is your part, it cannot be done automatically, because you should be able to determine which correspondent you trust. And you do that by entering a strong message key for your correspondent to start with.
In the subsequent message exchange, the Crypto Bone will take care of the message keys and you can forget about it, but to provide the initial secret should be entirely your own decision, because it lays the trust foundations for the message exchange.
Before we start to explain the technical aspects of the inner workings, it is necessary to explore the Crypto Bone from a user's point of view. Here is the ideal situation.
If you are interested in the technical aspects of the Crypto Bone's inner workings this explanation contains all the details.
