How Secure Is The Crypto Bone?
Fundamental Assumptions
First of all, security is not a binary feature. There is not one single thing you can do and as a consequence, you're secure. Security is not a product, but a process.And it is a process that requires constant vigility. You cannot buy a product and be secure. But you can do much more than most people do, and you can do so without having to become an expert.
Design Decisions
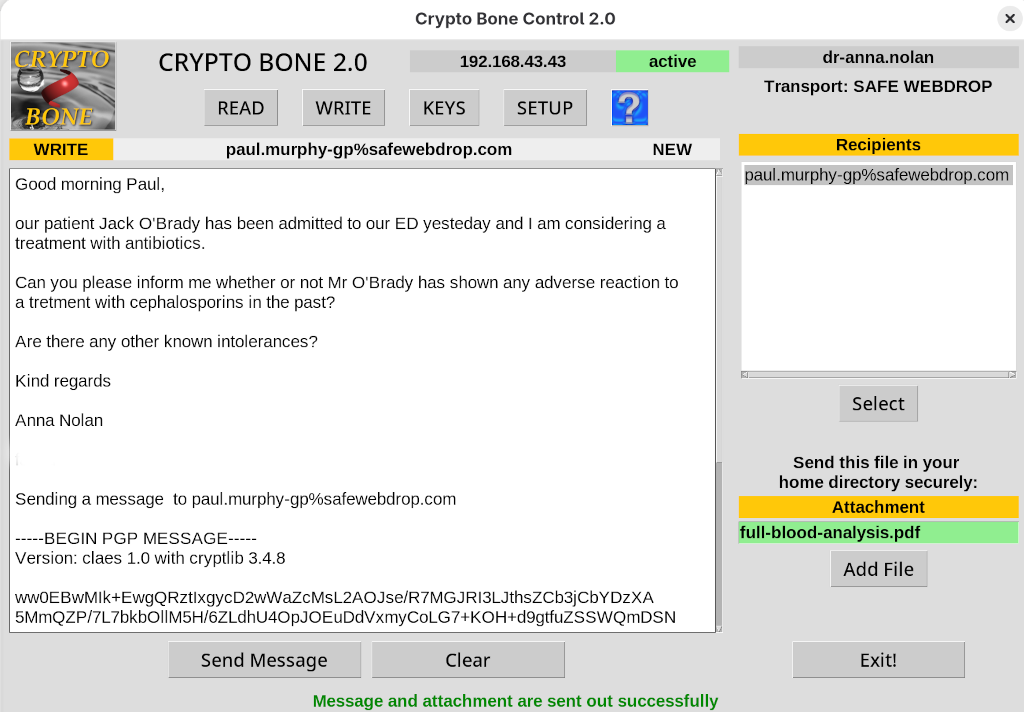
To be able to assess the security of the system, one has to understand how the Crypto Bone actually works.
I have prepared two pages that explain the underlying ideas:
The first explains the Crypto Bone from the user's view. It introduces the basic ideas behind the project without much technical detail.
You can read all about the technical details and implementation processes in the explanation from the technical point of view.
The Threat Model
But the essential questions must be answered based on a realistic and comprehensive Threat Model Analysis for the External Crypto Bone.How does the Crypto Bone respond to the numerous risks a secure encryption system has to cope with? Of course, this analysis will be in need of a constant update, to reflect recent developments and new risks.
Attacks on the Crypto Bone
There are a number of possible attacks on the Crypto Bone, that will be discussed in this analysis.
Have a close look at all these explanations and analysis.
